7 Which of the Following Ciphers Is Are Symmetric
View the full answer. C EKP and for decryption.

Symmetric Encryption Algorithms Live Long Encrypt Security Boulevard
A block cipher performs mathematical functions on blocks of bits at a time.

. Data Encryption Standard DES Affine Cipher Diffie-Hellman. A stream cipher is a cipher that uses a sequence or stream of different keys in order to encipher successive pieces of plaintext. Cryptography and Network Security.
You need to convert the given plain text into ciphertext under the Ceasar cipher encryption technique. Triple DES 3DES is the common name for the Triple Data Encryption Algorithm TDEA or Triple DEA symmetric-key block cipher which applies the Data Encryption Standard. Here we have a set of multiple-choice questions and answers quiz on ciphers in Cryptography basic concepts of Cryptography Techniques and different types of ciphers.
Electronic Code bookECB Cipher Block ChainingCBC Cipher FeedbackCFB Output FeedbackOFB and Counter Mode CTR Describe Electronic Code Book ECB related to symmetric block ciphers. DES cipher algorithm three times to. Data encryption standard des diffie hellman cipher.
If the message size is not a multiple of n then it should be divided into n bit blocks and the last. Please correct me if im wrong. Both random and sequential D.
Question 7 2 points Which of the following symmetric ciphers does is not used a to encrypt and decrypt. RSA is based on factoring composite numbers into their primes and ElGamal is based on discrete logarithms. For an 8021XEAP solution to work properly which two components must.
Break message into blocks and operate on a block-by-block basis Stream Ciphers. Examples include the Caesar simple substitution and Vigenere ciphers. Submitted by Monika Sharma on February 02 2020.
Abc will always equal fct. Symmetric encryption is a way to encrypt or hide the contents of material where the sender and receiver both use the same secret key. PSK authentication and 4-Way Handshake.
Block Ciphers Block Cipher A symmetric key modern cipher encrypts an n bit block of plaintext or decrypts an n bit block of ciphertext. When two different keys encrypt plain-text message to same cipher-text B. AES is a symmetric cipher and symmetric ciphers are not used in digital signatures.
A stream cipher on the other hand does not divide a message into blocks. The literature divides the symmetric ciphers into two broad categories. One key in a keyed hash function generates different message digests D.
That means an attacker cant see the message but an attacker can create bogus messages and. Which of the following methods of authentication must occur along withthe 4-WayHandshake in order to generate dynamic TKIPARC4 or CCMPAES encryption keysChoose all that applyB. AES Rijndael RC5 Block vs Stream Ciphers zThere are two main classes of symmetric ciphers.
O DES O AES O RC4 O WEP. We have an Answer from Expert View Expert Answer. 341 Stream Ciphers 342 Block Ciphers 343 Combination.
O DES AES RC4 WEP. Symmetric ones use the same key called a secret key or private key for transforming the original message called plaintext into ciphertext and vice versa. DES Cipher AES Cipher.
Data Encryption Standard also known as DES is a symmetric key block cipher that was introduced in the year 1977 by IBM. I am not sure about this question answer. Traditional Symmetric key cipherspptx.
For any block of plaintext the cipher is always the same eg. When one key encrypts a plain-text message into two different cipher text messages. Previous question Next question.
The two main types of symmetric algorithms are block ciphers and stream ciphers. A symmetric cipher is one that uses the same key for encryption and decryption. This problem has been solved.
Which of the following symmetric key encryption ciphers provides the strongest protections. Stream ciphers and block ciphers. P DKC so that the process is reversible.
Note that symmetric encryption is not sufficient for most applications because it only provides secrecy but not authenticity. Examples of this include Vigenères autokey cipher Subsection 332 and Vernams one-time pad cipher Subsubsection 5222. 8021XEAP authentication and 4-Way Handshake D.
Cryptography and Network Security. AES AES is the symmetric algorithm-of-choice for most applications today and is. Data Encryption Standard DES Affine Cipher Diffie-Hellman.
ZTypically block ciphers may be modified to run in a stream mode. Symmetric ciphers are generally faster than. 1 We are provided the plain text SUN.
Which of the following is not a type of symmetric-key cryptography technique. By necessity this single key must be kept secret from all but the sender and recipient so. See the answer See the answer See.
Identification of several keys used in symmetric key algorithms C. Which of the following symmetric key encryption ciphers provides the strongest protections. Question 7 2 points Which of the following symmetric ciphers does is not used a to encrypt and decrypt.
Process messages bit-by-bit or byte-by-byte as data arrives. Ciphers or algorithms can be either symmetric or asymmetric. Although the definitions are normally applied to modern ciphers this categorization also applies to traditional ciphers.
Bit Addition Cell Subsection 713 Key Streams Definition 7123. When the same keyis used for encryption and decryption the cipher is said to be a Symmetric Cipher. Both methods provide roughly the same strength per bit.
Symmetric ciphers are ciphers that use the same key to encrypt and decrypt ie for both the encryption and decryption algorithms. If the message has fewer than n bits padding must be done to make it n bits.

What Is Symmetric Key Cryptography Encryption Security Wiki
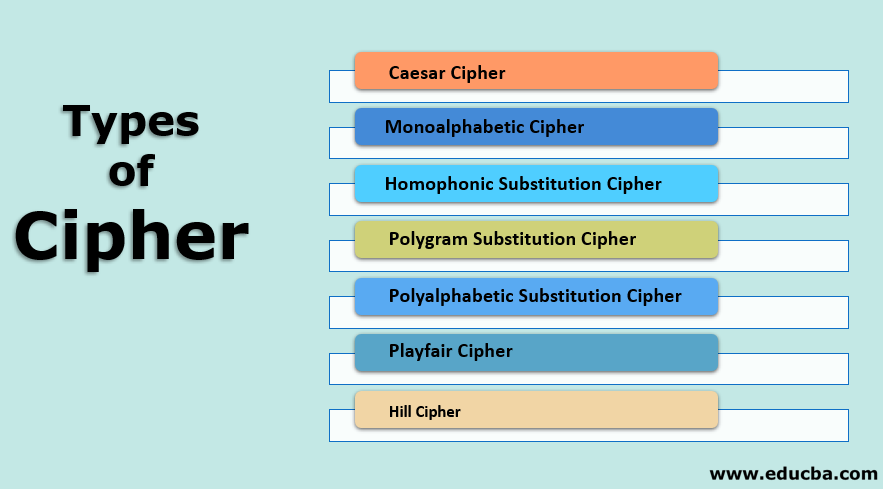
Types Of Cipher Learn Top 7 Various Types Of Cipher In Depth
No comments for "7 Which of the Following Ciphers Is Are Symmetric"
Post a Comment